Internet Surveillance and How to Keep Your Activity Private
Surveillance enables government bodies to gain detailed insights into individuals’ activities. Although its primary intent is often to prevent terrorism or other serious crimes, surveillance is increasingly becoming routine. As a result, many people have grown accustomed to it and show little concern.
While some forms of internet surveillance are illegal and many others are questionable, a significant portion is legal and conducted by governments, ISPs, and internet services. Companies like Google and Facebook also use surveillance to sell targeted advertising based on users’ interests, habits, and personal information.
In this article, we’ll explore the organizations that perform internet surveillance, their methods, and steps you can take to minimize the data collected about you.
Who can monitor your online activity?
Predictive Models https://t.co/Y0ztp8umzA https://t.co/56Hf69fI26 pic.twitter.com/rTF3BqknVU
Privacy Affairs March 23, 2023
The government has access to a lot of sources
Ever since the Edward Snowden revelations of 2013, in which he leaked details of the massive, ongoing surveillance activities of both US and foreign government agencies, the general public have been aware of just how much data these agencies hold and store about us.
The government has, however, done an incredible job in minimizing fallout. People seem to have gotten used to the fact that nothing they do online is ever truly private.
It’s almost as though the gradual erosion of privacy has led us to be apathetic towards ever-increasing invasions into our personal lives. The fact that there hasn’t been any real protest against the proposed porn-block in the UK is evidence of this.
We don’t know how government agencies in the US, UK, Canada, etc., can monitor individuals, but it’s safe to say that we’d be very concerned if we did know.
We have to look at examples we’ve already known for a few years.
In 2014 we were told that the NSA and GCHQ could map every single internet-connected device on the planet. That’s right; they know the precise physical location of the personal data connected to every laptop, desktop, mobile phone, etc., on the planet.
Thanks to Snowden, we also know that the NSA has been able to spy on Skype calls for over a decade.
So yeah, governments have incredible surveillance capabilities and are showing no signs of slowing down their assault on privacy.
ISP tracking
Your internet service provider can monitor your online activity if it wants to, and probably often does.
ISPs record information about which websites you visit, which links you click, and even data you send to websites that aren’t secured by HTTPS.
They sell your data to advertisers, work with intelligence agencies, and monitor which services you use. Many ISPs, for example, want to keep track of which users are downloading or sharing torrents via P2P networks and will often throttle the bandwidth of users it thinks are doing so.
To primarily protect yourself from ISP monitoring, use a VPN to encrypt all your data so they cannot see the contents of your online activities. This will stop them from seeing which websites you access too.
ISPs will still be able to see if you’re sending or receiving data through P2P networks (torrents), but some best VPN services, such as NordVPN, provide obfuscated servers that hide the type of data being transmitted. See our NordVPN review for more information.
Google tracks you across the internet
If you’re a regular user of the vast array of Google services, like billions of people worldwide, you might be shocked at just how much information the company stores about you.
Every video you’ve watched on YouTube, every page you’ve ever visited or search you’ve made when logged into your Google account, the contents of your emails, and which ads you click, they know it all.
If you carry Google around in your pocket, in the form of an Android phone, practically every move, you make.
Google is a giant ads platform, with millions of websites using their services to both be found and generate revenue by allowing Google to place targeted ads on their sites. Chrome in particular is known for its eagerness to allow websites to track you for ad purposes.
Social media agencies track you too
As if you could have not noticed, with Facebook accused of mass surveillance, and the Cambridge Analytica scandal, social media networks exist solely to make money through ads targeted towards people based on their behaviours, interests, friends, location, and many other demographics.
What’s scary is the sheer amount of information people are willing to share on social: Everything from intimate details of their lives to vacation plans, family information, and more.
And you know those quizzes that help you determine what type of cheese you are or your heavy metal stage name? They’re a goldmine of information for anyone building up a profile of you for use in an identity fraud attack.
How do they do it?

Government agencies tend to be quite secretive about their capabilities, which is why it’s so hard to tell precisely how advanced their surveillance is. Still, you can bet that it’s come a long way since the Snowden revelations.
Some standard techniques and technologies allow not just governments but your ISP and potentially search engines and social media companies to keep their watchful eyes over you almost all the time.
Deep packet inspection
Deep packet inspection (DPI) is a method of processing data. Data packets (how information travels around the internet, between your router and ISP, etc.) are analyzed and evaluated before deciding what to do with them.
DPI is a vital aspect of anti-virus and firewall protection because it works in real-time and can block unwanted payloads or intruders entering the system. It can also be used to prioritize certain internet traffic types.
So far, so good, right?
Well, DPI can also be used for more sinister purposes.
With this ability for a high-level analysis of data packets, it is also possible to monitor online activity as part of a surveillance operation.
DPI for surveillance purposes is most likely performed by a government agency or an ISP if instructed to do so by law enforcement. However, it is also a favorite of hackers carrying out a man-in-the-middle (MITM) attack.
What is a man-in-the-middle attack?
MITM is a type of cyber attack whereby the attacker positions themselves between the sender and recipient of data. For this article, we can think of it as someone intercepting data between your computer and the website you’re visiting.
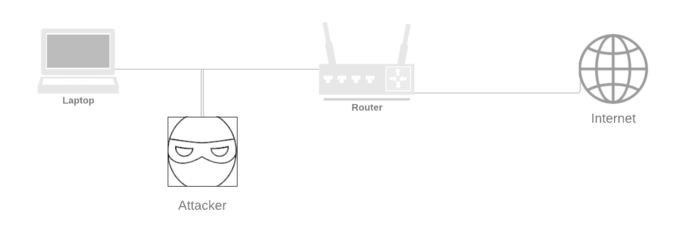
This could be information you’re entering on websites or sending messages through unencrypted channels.
Fortunately, most prominent online services such as Facebook, Messenger, Amazon, and all reputable websites, use TLS to encrypt all traffic between the web browser or app and their servers. This means that a MITM attacker would only be able to see the name of the service you’re using and a load of encrypted data.
This is useless information unless they’re building a profile of the services you use to perform a more sophisticated social engineering attack.
Governments, however, may be able to access server logs of websites and therefore discover the exact time of specific communication, which could point to a user’s actions. In this case, the protection of encryption is irrelevant.
Browser fingerprinting
Every time you visit a website, your browser sends detailed information about your computer, browser and settings, location, etc.
This information includes your language settings, cookies, previous webpage if you followed a link, screen resolution, installed plugins, enabled fonts, etc.
All of these put together will often create a profile that’s totally unique to you, like a fingerprint.
Now, the thing that makes browser fingerprinting so scary – it can be performed by any website you visit. What’s more, it’s extremely accurate.
The main threat to privacy from browser fingerprinting is persistently targeted ads from agencies using your browsing habits as markers to link you with companies.
Governments almost certainly also use browser fingerprinting when surveilling a target.
Finally, while many people assume that using a VPN will keep their information private, that’s not the case – VPNs do nothing to mitigate the threat of browser fingerprinting.
Cookies
Cookies are tiny text files that many websites save to your browser.
They’re mostly harmless and contain information such as a login command, so you don’t need to keep entering your password each time you visit Facebook.
Cookies are also used to track you across the internet. Companies such as Google and Facebook drop a cookie on your browser whenever you visit websites advertising through them. This is then used to display targeted ads to maximize profitability.
Targeted ads aren’t the most worrying form of online surveillance, although the problem occurs when companies like Google and Facebook store enormous amounts of data connected with each individual.
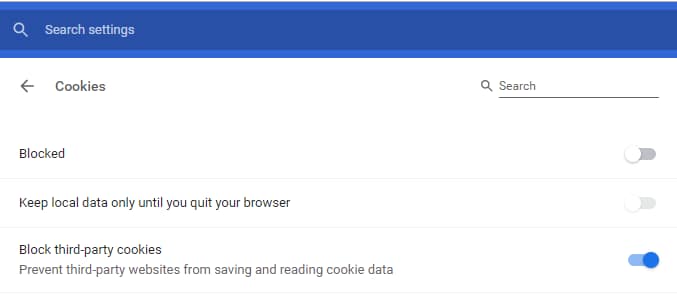
How to block cookies in Chrome
You can actually block cookies in Chrome, by default. Here’s how:
- 1. Click the three dots under the X in the top right of chrome, then choose “settings”
- 2. Scroll down to the bottom of the settings tab, and click “Advanced”
- 3. Now scroll down until you see “Site Settings”, click there, then on the next page, click “Cookies”.
- 4. For the most private setup, choose the following:
This will make your browsing experience a bit more annoying, as you’ll suddenly be logged out of everything, but you can add sites to a whitelist under “Allow” at the bottom of that page.
Another option is to use Firefox and privacy addons or private browsers. Keep reading to find out how.
reCaptcha V3
Are you a robot?
Chances are you’ve had to prove you’re human at some point. More than 4.5 million websites use reCaptcha to block bots and automated scripts from accessing their pages.
Fighting spam does help make the internet a better place. Still, with so many websites using a service from a single company, questions are raised about whether that company is acting in users’ best interests.
Especially when that company is Google, who have already fallen foul of privacy regulations in Europe.
Google recently introduced rCaptchaV3, which does away with the user confirmation box, and instead is based upon collecting masses of data and creating profiles of how people interact with websites.
Rather than just your mouse clicks and how you navigate through websites, reCaptchaV3 appears to collect personally identifiable information, such as those gathered during browser fingerprinting, along with reading cookies installed on your browser.
This essentially allows Google to track individuals across a vast range of web properties not directly associated with the company. It’s one of those – how much information are you comfortable sharing with Google – questions.
App vulnerabilities
App vulnerabilities are weaknesses in an app’s code that attackers can exploit to compromise security and facilitate cybercrime.
Mobile apps are ubiquitous, and millions are installed by mobile users worldwide daily. Many common attacks are targeted at these apps; unfortunately, many apps aren’t built with security.
Targeted apps range from Facebook games in which developers can leverage Facebook’s user base to market their app, as happened during the Cambridge Analytica scandal, to simple apps such as WhatsApp, which was discovered to have a vulnerability allowing attackers to inject surveillance software onto users’ devices.
The only way to minimize the threat of internet surveillance resulting from app vulnerabilities is to use minimal apps – uninstall anything you don’t use – and make sure your apps are up to date.
Malware
Malware is a broad term that includes viruses and other malignant software.
All malware compromises the security of the infected device. Many forms of malware are used to monitor users to steal personal data or allow governments to access information on a target individual.
The US government has a long list of secretive malware they use to spy on citizens without their knowledge. Again, these things come up; people are momentarily outraged and forget.
Just go back to the top of this page and check the link to the Edward Snowden revelations to see all the malware information he leaked in 2014.
While the US denies monitoring citizens, the Chinese government doesn’t seem to care. Travelers have recently been forced to install malware on their devices that gives access to pretty much everything.
How to hide from surveillance
So, do you feel like someone’s watching?

It’s pretty hard to tell for sure. But here are a few ways to make it harder to track your activity and mitigate the threat of online surveillance:
Monitor network connections
You can use a service such as GlassWire to monitor connections to your computer, but if you really want to dig deeper, follow the instructions here.
If you have a more advanced router than your standard ISP-provided one, you can set up rules and blocking to help protect you, along with a firewall and antivirus on the router itself.
Ditch Google – use a private browser and search engine
If you haven’t noticed, Google collects a huge amount of your data.
Google is very convenient – search, email, storage, backup, and many other things are handled in a central location. But the cost is your privacy. If you’d prefer to avoid this, consider changing your services.
So one way to instantly increase your privacy is your using private browsers and search engines that are explicitly built to protect your privacy rather than profit from your details.
Use a VPN
A VPN protects data as it travels between your device and the internet by applying strong encryption that is pretty much uncrackable. I say here because, once again, the NSA wants to crack it, and we don’t know if they can yet.
As far as we know, the encryption used by the best VPN services is still uncrackable.
So that stops anyone from seeing what data you’re sending and receiving. Still, it also helps you go undetected by changing your IP to that of the VPN server you’re connected to, so you’re physically located there.
This helps you avoid censorship or activity-based surveillance, although it’s not foolproof, as I’ve already stated.
A VPN doesn’t make you anonymous online. It simply adds a layer of protection that significantly increases your privacy.
Other methods to match activity to a user, such as browser fingerprinting and malware, are still effective when using a VPN.
Use antivirus on your phone and computer
Do people still use antivirus?
They should. They definitely should.
The biggest threats to online privacy can be thwarted by up-to-date malware protection.
Make sure to use a quality antivirus on both your computer AND phone, and please make sure it updates frequently.


4 Comments
Yakubu
September 2, 2022 12:56 pm
Great article, Miklos. Please, I want to cite this article in my college discussion class.
Miklos Zoltan
September 7, 2022 11:02 am
Sure, that’s fine. 🙂
Ashley Jones
May 9, 2022 4:25 am
Wow! Thank you! I constantly wanted to write on my site something like that. Can I take a portion of your post to my website?
Miklos Zoltan
May 11, 2022 9:20 am
If you credit us, sure!