
uBlock Origin on Firefox can now block first-party tracking scripts that attempt to bypass filters and rules by utilizing DNS CNAME records to load scripts from a third-party domain.
A first-party tracker is when the tracking script is located on the same domain as the web site, while a third-party tracker is when the tracking script is located on another domain.
As browsers begin to block third-party trackers as part of their tracking protection features, some web sites have switched to first-party trackers in order to bypass these protections.
In a new issue posted to the uBlock Origin ad blocker's GitHub issues page, a user posted a new issue about a web site loading tracking scripts from a subdomain of the site, which makes it look like a first-party tracker.
According to the user, though, this subdomain was actually a DNS CNAME record that resolves to a different domain that provide tracking services.
As uBlock Origin is seeing these as a first party tracking scripts being loaded from the website's domain, it does not block them and allows them to run.
First-party tracker protection only available in Firefox
In order to block first-party trackers that utilize CNAME records, uBlock Origin would first need to perform a DNS lookup of the hostname loading a script to determine the underlying domain that it resolves to.
For example, if a script is being loaded from the user's domain, the ad blocker will perform a DNS lookup and check if it resolves to known tracking domains, and if so, block them.
Unfortunately, Chrome does not provide an API that allows an extension to perform DNS lookups, but uBlock Origin developer Raymond Hill was able to find an API in Firefox that could perform this function.
"I am looking at https://developer.mozilla.org/en-US/docs/Mozilla/Add-ons/WebExtensions/API/dns/resolve, it can be used to expose the CNAME:"
Hill later released uBlock Origin 1.24.1b0 that contains a new feature that will "uncloak" CNAME records in order to block first-party tracking that utilizes scripts on third-party domains.
"If using 1.24.1b0 and above, to "uncloak" actual (canonical, CNAME) hostname, set advanced setting cnameAliasList to *.
Network requests for which the actual hostname differs from the original hostname will be replayed through uBO's filtering engine using the actual hostname. When I started developing the feature I could spot eulerian.net in the logger when visiting https://www.liberation.fr/, but I can no longer reproduce this. Regardless, uBO is now equipped to deal with 3rd-party disguised as 1st-party as far as Firefox's browser.dns allows it."
With this new feature added, if using uBlock Origin version 1.24.1b0 or newer, when installing the extension it will require a new DNS permission described as "Access IP address and hostname information", which will be used by the extension resolve the CNAME records.
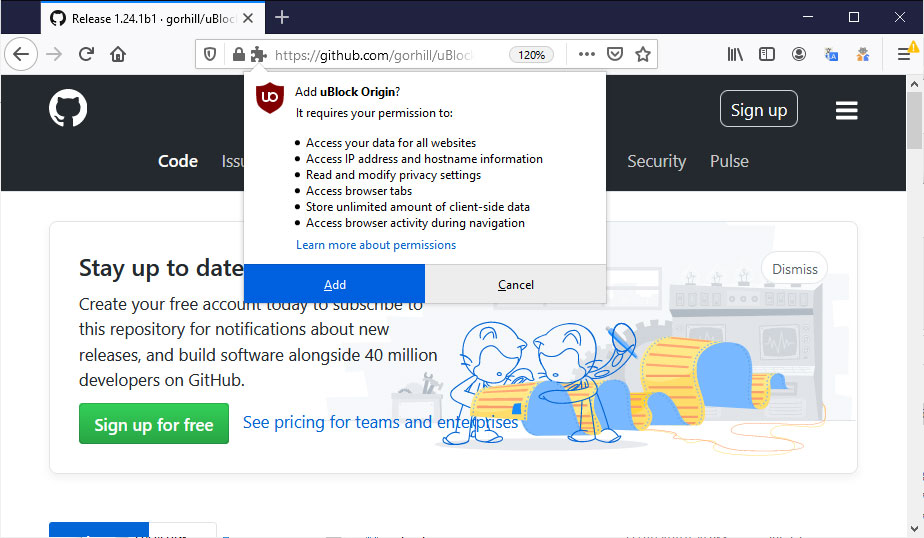
Users can then enable this feature by following these steps:
- Go into the extension's Settings.
- Put a checkmark in the "I am an advanced user (required reading)" checkbox and click on the
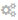 icon.
icon. - When the Advanced settings page opens, find the cnameAliasList setting and change it from 'unset' to '*'.
When finished making the changes, it should look like the image below.
With this new setting enabled, any first-party trackers that use CNAMES to third-party domains will be unmasked and blocked.


Comments
Throwdown - 4 years ago
uBlock Origin is a great tool to block unwanted scripts and of course ads. I prefer it over Ad block plus and I have added tons of custom domains to it for one reason or another. I'm really not that opposed to ads that are placed correctly. Some sites are overrun with them and it makes the site useless to navigate.