- Home
- Windows
- Windows IT Pro Blog
- Extended Security Updates (ESUs): Online or proxy activation
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
When your Windows products reach the end of support, Extended Security Updates (ESUs) are there to protect your organization while you modernize your estate. To take advantage of this optional service, you’d purchase and download ESU product keys, install them, and finally activate the extended support.
Note: People tend to refer to ESU keys interchangeably as multiple activation keys (MAK), ESU product keys, or ESU license keys. |
Ultimately, you can activate the ESU product key with or without internet connection. For online activation, you can use the elevated command prompt or Volume Activation Management Tool (VAMT). To install and activate ESU for devices that are not connected to the internet, you can use VAMT or phone activation. Azure Virtual Machines (VMs) are a special case, which we’ll touch on toward the end. We’ll use the Windows Server 2012 R2 case to illustrate ESU key activation. Let’s start with the easy steps for connected servers.
Important: Activation via Control Panel > System and Security > System > Activate Windows activates the Windows operating system only. You cannot use it to activate ESU keys. |
Get started with Volume Activation Management Tool (VAMT)
You can use Volume Activation Management Tool (VAMT) for online and/or proxy activation. To install and activate ESU keys using VAMT, follow these steps:
- Download and install the Volume Activation Management Tool.
- Download the VAMT- ESU configuration file and update your VAMT configuration file.
- Configure the client device’s firewall for VAMT.
- Add the ESU product key to VAMT.
- Select the product, right-click it, select Activate, and then select your activation method.
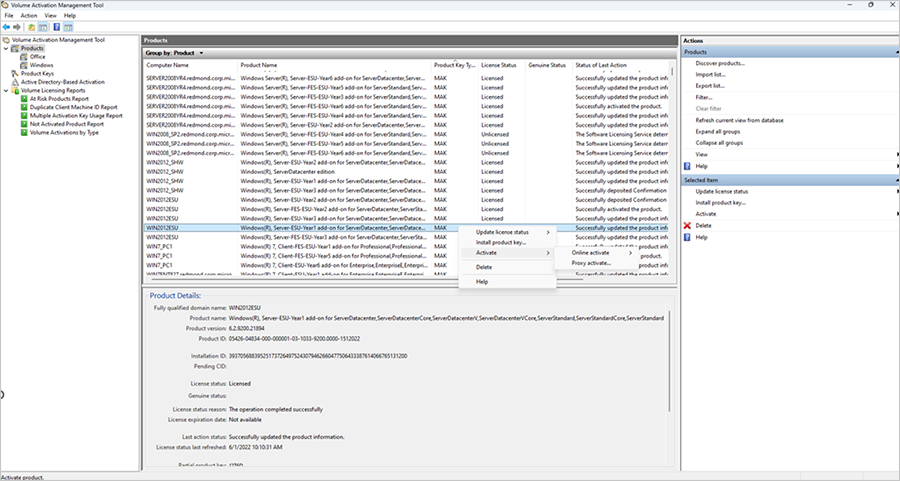
Activate ESU keys online with VAMT
If the VAMT host (with internet access) and Windows Server 2012/R2 servers you want to activate with the ESU keys are on the same network, you only need one VAMT host. In this case, no need to move the VAMT data file exported into .cilx file for activation.
Note: For online activation, make sure the device has access to the following endpoints: |
- https://activation.sls.microsoft.com/BatchActivation/BatchActivation.asmx
- http://go.microsoft.com/fwlink/?LinkId=82160 (This FWLink redirects to the above URL.)
If you directly click or tap on these links, you’ll receive a privacy error message. This is the expected behavior. |
The VAMT host connects to the device using Windows Management Instrumentation (WMI) port 135. This includes RPC over TCP/IP (49152 or above), as described in The default dynamic port range for TCP/IP has changed in Windows Vista and in Windows Server 2008. Please ensure that this and any other ports are open for any physical firewall or router between the VAMT host and the device. This includes any software-based firewall on the device. If you’ve followed the allow-listing steps in Windows Server 2012/R2 Extended Security Updates, you’re all set to activate ESU keys online with VAMT.

Learn more about this scenario at Perform Proxy Activation.
Use proxy activation offline with VAMT
If you cannot put that VAMT host on the same network, then you need a second VAMT host. Please check that you have what’s required for this scenario before going through the activation steps:
- VAMT host with internet access (let’s call it “VAMT online”), which doesn’t need to be on the same network as the Windows Server 2012/R2 devices.
- VAMT host on same network as the Windows Server 2012/R2 devices that you want to activate but which don’t have internet access (let’s call it “VAMT offline”).
- The ESU product key
To activate the ESU keys with VAMT proxy, let’s create your setup and walk through a series of steps.
Prepare for proxy activation offline
- Configure Windows Firewall on the Windows Server 2012/R2 devices to allow Windows Management Instrumentation (WMI) through firewall. Go to Windows Firewall > Allow a program or feature through Windows Firewall. Select the Windows Management Instrumentation (WMI) checkbox. Press OK.
- Make sure that the user logged into the VAMT offline host is also admin on the Windows Server 2012/R12 devices. If not, you can use the alternate credentials option when connecting to devices. You’ll usually find this option in the UI wherever you’re doing some action on a device (e.g., VAMT interface to update license status, Install Product Key configuration, Proxy Activate dialog box).
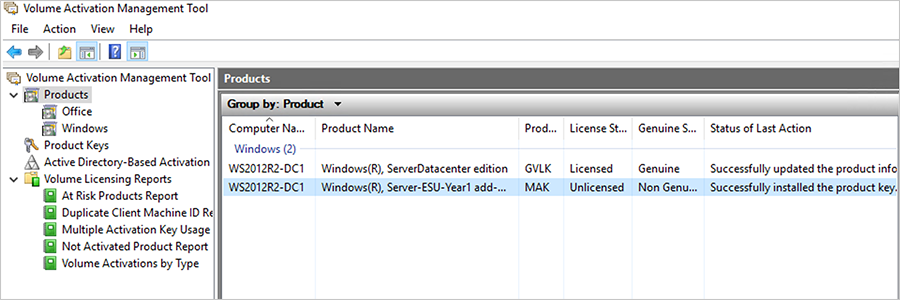
- Add the Windows Server 2012/R2 device to the VAMT offline host. In VAMT, right-click Products > Discover products… > Manually enter name or IP address.
- Right-click Product > Update license status to update the license information for the client device.
- Add Server-ESU-Year1 product key on the VAMT offline host by right-clicking Product Keys > Add product keys…
Perform proxy activation offline
- Install Server-ESU-Year1 product key on the client computer. Right-click Product > Install product key…
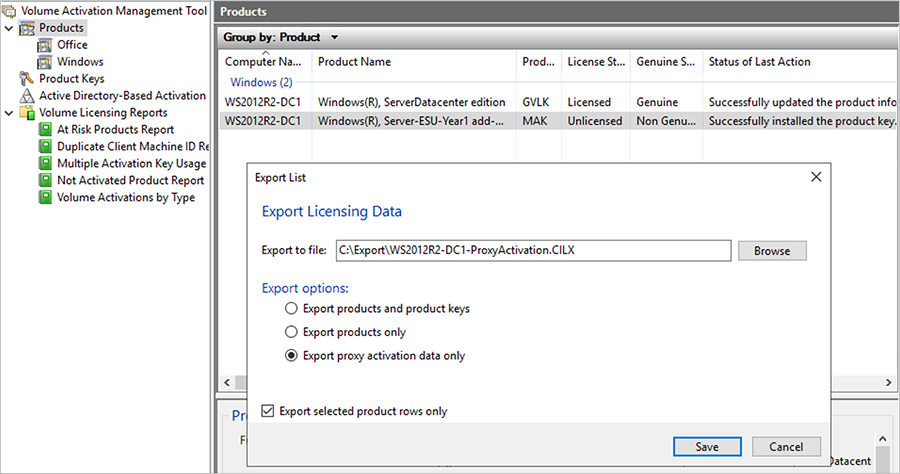
- On the VAMT offline host, export VAMT data with installation IDs to a .cilx file. Then copy this .cilx file to the VAMT online host. Select the individual product (client computer) that received Server-ESU-Year1 key in the previous step. In the Actions pane on the right, select Export list. Select Export proxy activation data only under Export options. Check Export selected product rows only option and save it to a file. Copy this .cilx file to some removable media. Note: For information on what’s in the exported file, see Import and export VAMT data.
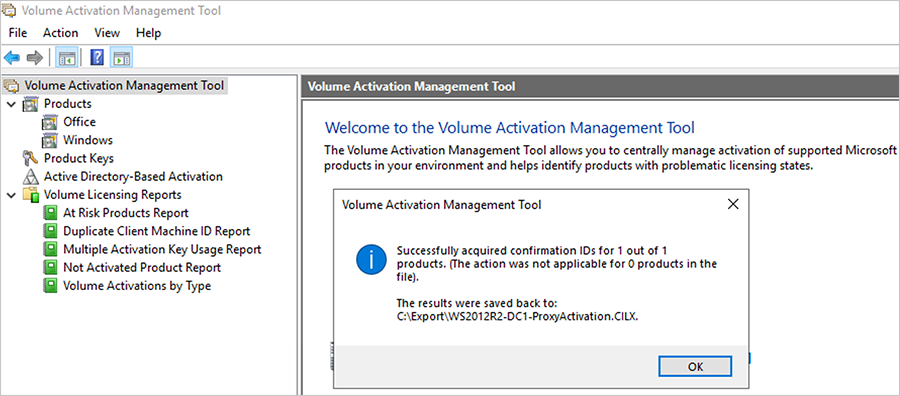
- Acquire confirmation IDs from Microsoft activation servers. Insert the removable media that contains the .cilx file exported from the VAMT offline host into the VAMT online host with internet access. Open VAMT and make sure you’re on the root node. In the Actions pane on the right, select Acquire confirmation IDs for CILX. In the Acquire confirmation IDs for file dialog box, navigate to the location of the .cilx file that you exported from the isolated lab host computer. Select the file and press Open. You’ll see an “Acquiring Confirmation IDs” message. Once the acquisition is complete, review the VAMT message that shows the number of confirmation IDs acquired and the file where you saved the IDs.
- Save confirmation IDs on the host device without internet access. Note that results are saved to the same file, so it’s not necessary to export. Remove the media that contains the .cilx file from the VAMT online host and insert it into the VAMT offline host. Import the .cilx file. In the Actions pane on the right, select Import list. In the Import list dialog box, navigate to the location of the .cilx file that contains the confirmation IDs. Select the file and then press Open. Notice a VAMT message that states “Data import has completed successfully.”
- All that’s left to do is apply the confirmation ID and activate the product.

For more details, refer to Scenario 2 Proxy Activation and Perform proxy activation.
Activate ESU keys via phone
To activate ESU keys via phone, use the Slmgr.vbs command options /dti and /atp.
- Open an elevated command prompt.
- Type slmgr.vbs /ipk <ESU MAK Key> and select Enter to install the product key.
- Get the Installation ID for the ESU Key using the corresponding ESU Activation ID (see Windows Server 2012/R2: Extended Security Updates for a table listing each program). For example:
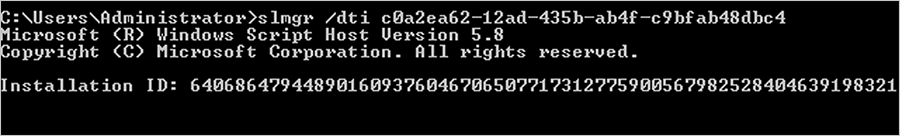
- Once you have the Installation ID, call the Microsoft Licensing Activation Center for your region. They’ll walk you through the steps to get the Confirmation ID. Make a note of your Confirmation ID. You can also request to receive a text message with a link to a web page where you can look up your Confirmation ID by entering the Installation ID. The link can only be used for two devices at a time.
- Type slmgr /atp <Confirmation ID> <ESU Activation ID> to activate the ESU SKU using the Confirmation ID obtained in the previous step.
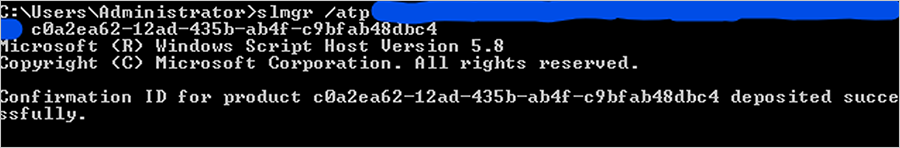
- Type slmgr /dlv <Activation ID> or slmgr /dlv all and select Enter to verify that the License Status shows as “Licensed.”
Easy-to-no activation for Azure virtual machines
The good news is that you don’t need to deploy an additional ESU key for Azure virtual machines (VMs), Azure Stack HCI, version 21H2 and later. Like on-premises devices, you’ll need to install the appropriate SSUs as outlined in Windows Server 2012/R2: Extended Security Updates. With those SSUs, VMs will be enabled to download the ESU updates.
Would you ever need to deploy the ESU key for Azure products? Yes. You’ll do this for Azure VMWare, Azure Nutanix solution, Azure Stack (Hub, Edge), or for bring-your-own images on Azure for products under extended support. Just follow the steps to install, activate, and deploy ESUs described in Windows Server 2012/R2: Extended Security Updates.
Ready to activate your extended security updates?
Use any of these activation scenarios today to protect any Windows devices that reach the end of support for a limited time. The illustrative case is especially helpful today for Windows Server 2012, Windows Server 2012 R2, and Windows Embedded Server 2012 R2 as they reach end of support. Our recommended solution is Windows Server 2012 Extended Security Updates enabled by Azure Arc. Read Windows Server 2012/R2: Extended Security Updates for recommendations and steps as you modernize your estate and shift to Azure.
For additional information, consult Product Lifecycle FAQ - Extended Security Updates.
Continue the conversation. Find best practices. Bookmark the Windows Tech Community, then follow us @MSWindowsITPro on X/Twitter. Looking for support? Visit Windows on Microsoft Q&A.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.