The Security Model That Forges A Foundation For Business Growth
You don’t need to understand the granular details of Zero Trust security to understand why it’s so effective or how it can help power a radical change in technology capabilities that creates the foundation for trusted business. With Zero Trust, security becomes a business amplifier, and the CISO transitions from your organizational bête noire to a sought-after colleague and supporter. We explain Zero Trust fundamentals for C-level executives, detail Zero Trust’s business benefits and competitive advantages, and explain why every business leader should be a Zero Trust champion.
Author:
Stephanie Balaouras
Contributors:
Joseph Blankenship, David Holmes, Paul McKay, Jess Burn, Alexis Tatro, and Michael Belden
Zero Trust Security Means Business: Then And Now
Forrester developed the model and coined the name Zero Trust in 2009 as a much-needed alternative to older perimeter-based security models. The model became the gold standard among security teams working to defend against devastating breaches. As the model gained widespread adoption, governments across the globe began mandating it for their agencies while cybersecurity vendors began tailoring their product roadmaps (and their messaging) to capitalize on its growing popularity. Vendor hype sowed confusion and fostered cynicism amongst security leaders who questioned whether Zero Trust was anything more than just a buzzword.
But Forrester’s Zero Trust principles and its core conceptual model have always remained consistent (see Figures 1 and 2). More importantly, Zero Trust has always been about more than cybersecurity. In today’s world where businesses must move at the new speed of digital customers (whose trust is up for grabs), the following business benefits of Zero Trust should motivate even the least cyber-savvy business leaders to become ardent champions.
- Zero Trust security engenders brand trust. First, paradoxically given its moniker, adopting Zero Trust is foundational to becoming a business that customers, employees, and partners trust, because it blunts one of the prime causes of trust erosion — security breaches. It’s also a means by which companies can build trust by powering all seven levers of trust. We know from our research that an individual’s level of trust in a company drives revenue-generating behaviors such as the likelihood to purchase again, prefer the company over competitors, try unrelated products and services, and share personal data.
- Zero Trust accelerates new engagement models and emerging technologies. Second, Zero Trust is the only security model fit for evolving business paradigms and the rapid integration of emerging technologies. Whether the intent is to cocreate tomorrow’s immersive experiences with partners or develop new platforms using cloud-native tech, we designed Zero Trust for the boundaryless enterprise, and its core principles easily adapt to future scenarios. This is why Zero Trust is integral to any organization that wants to mature to a future fit technology strategy — a customer-obsessed approach to technology that enables adaptivity, creativity, and resilience.
- Zero Trust boosts customer and employee experience for growth. Lastly, because Zero Trust requires security teams to have a detailed understanding of business use cases and customer journeys to target optimal security policies, your Zero Trust deployment becomes an expression of customer obsession in security terms. Normally, we talk about the trade-offs between better security and seamless user experience (UX), but when organizations deploy Zero Trust, it’s one of the rare situations where there isn’t a trade-off — Zero Trust not only improves security, it also improves UX. It also gives the organization the confidence to expand into new markets, form new partnerships, and make strategic acquisitions without taking on too much risk.
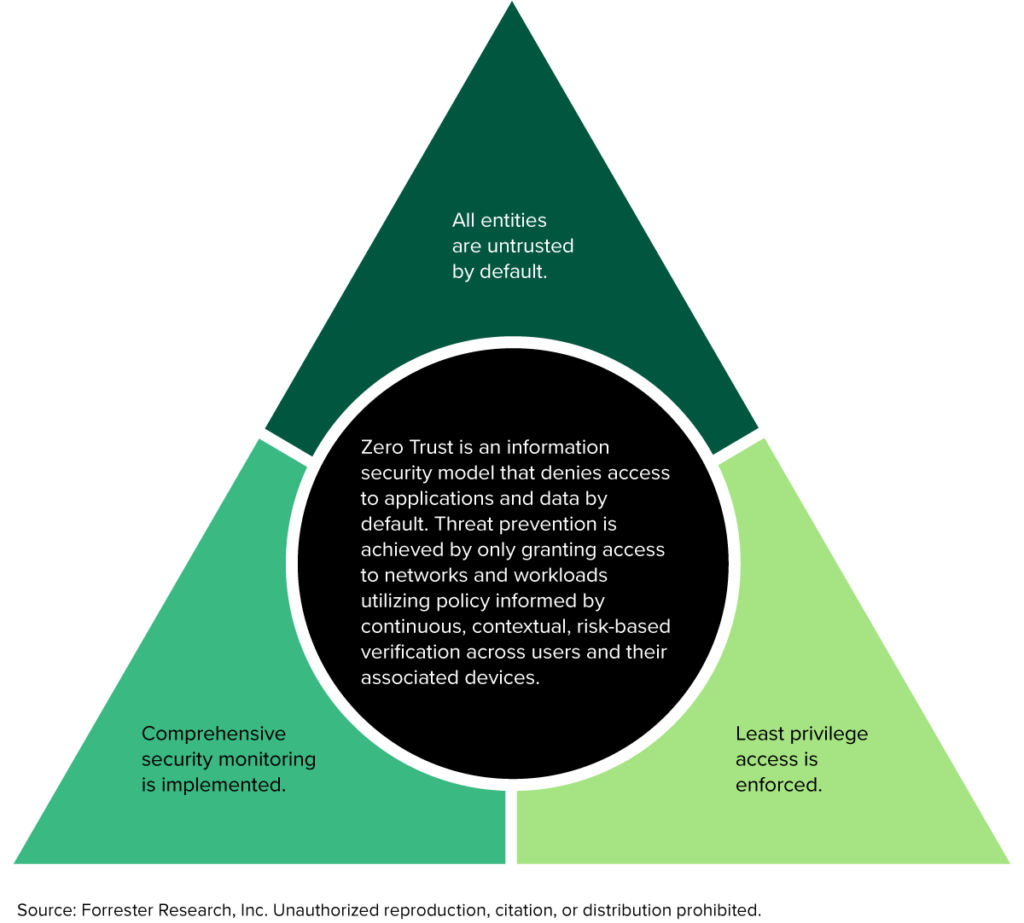
Figure 1
The Definition Of Zero Trust And Its Core Principles
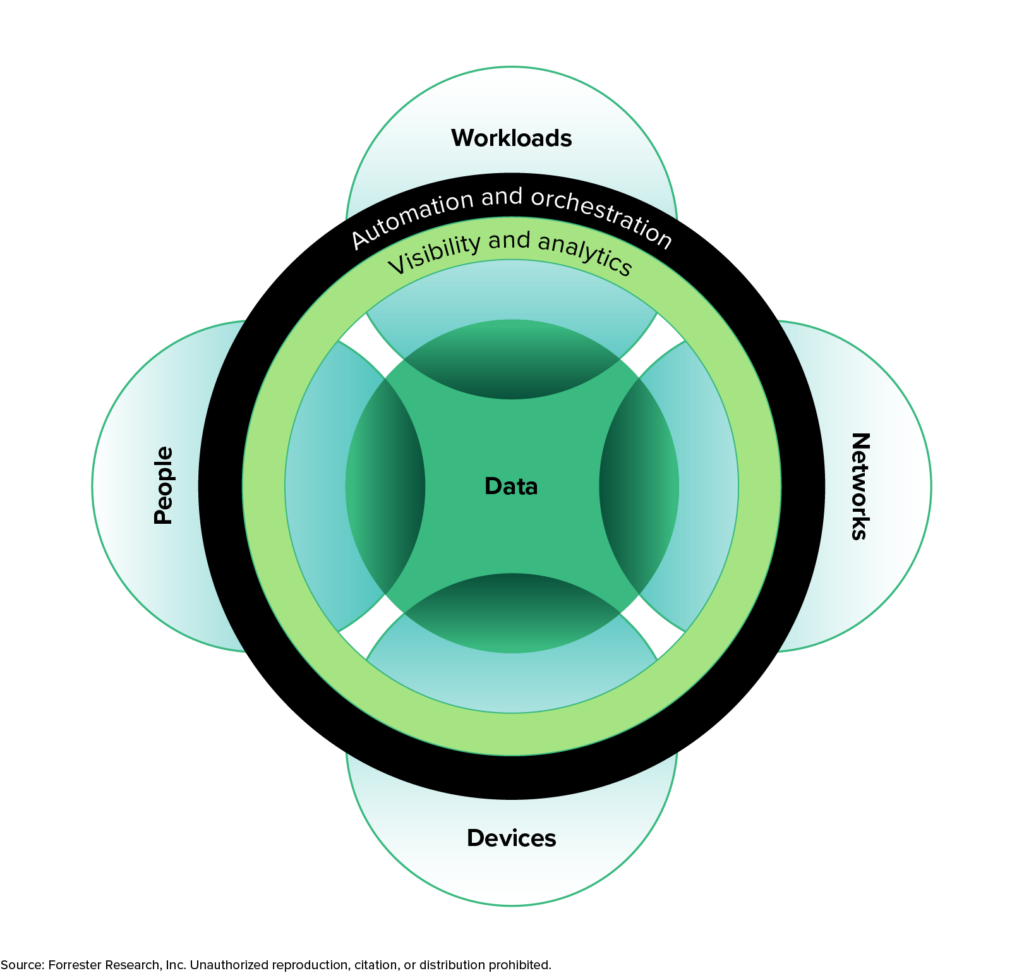
Figure 2
Forrester’s Zero Trust Model Of Information Security
Zero Trust Engenders Brand Trust — Among People, Not Packets
Many leaders balk at the term Zero Trust because they believe it implies organizations shouldn’t cultivate trusted relationships. This is the exact opposite of its intent. Forrester coined the name Zero Trust in 2009 because we wanted security teams to eliminate the dangerous trust assumptions that were making devastating breaches the norm. By treating all traffic inside the corporate network as trusted by default, security teams ignored threats from malicious insiders, privileged partners, and compromised user accounts responsible for a high percentage of breaches. This also meant security teams never actively looked for tell-tale signs of cybercriminals already inside the network. In 2009, it wasn’t unusual for attackers to dwell undetected for months with free rein to pilfer customers’ sensitive data and the enterprise’s most valuable IP, forcing customers to cope with crippling identity theft and the business to cede competitive advantage. The name Zero Trust is a reminder to security teams to never trust the packets traversing the network and to adopt a posture of vigilance that presumes the enterprise has already suffered a breach. With a Zero Trust approach, business leaders can:
- Increase customer data sharing to power new experiences. Forrester’s Consumer Trust Imperative Survey, 2023, shows that online adults in the US (38%), Spain (28%), Italy (47%), and Singapore (36%) are likely to share more of their personal data with tech companies they trust. Zero Trust reduces the likelihood that anyone can intentionally or unintentionally abuse customers’ personal data. This makes it easier for business leaders to communicate with customers about a company’s privacy practices clearly and openly, building confidence in the company’s commitment to privacy. With more data, tech companies can beat competitors to market with anticipatory experiences that deliver convenience to customers — simplifying or even eliminating required interactions.
- Successfully introduce new products. According to the same survey, more than half the online adults in the US, Spain, Italy, and Singapore would be willing to try new products from a tech company they trust. Zero Trust is a data-centric and workload-centric security model; it requires organizations to not only protect customer-facing technology and services in production, but also ensure new offerings have a minimum viable set of security features built into them by design — not after the fact. Zero Trust security doesn’t slow time to market; it balances time to market with customer requirements for privacy and security while minimizing risk to customers and the business itself.
- Preserve customer loyalty and retention. We also know what undermines trust — security and privacy breaches. Consider that online adults in the US (22%), Spain (33%), Italy (32%), and Singapore (26%) say that they would stop doing business with a company/organization permanently if they see news about a data breach exposing customers’ personal information. Zero Trust won’t stop all breaches, but it will decrease the frequency and scope of the impact, and with its emphasis on data protection, there’s a good chance a breach will never expose unencrypted customer data. When companies build up trust with customers, customers are much more likely to forgive the company for mistakes, but it’s better to avoid spending that trust capital on breaches you can easily avoid, and instead use it to experiment with new offerings or new experiences powered by emerging tech.
Zero Trust Accelerates New Engagement Models And Emerging Technologies
With traditional perimeter-based security, you build ever higher walls around everything, making it difficult to do business while leaving yourself exposed when defenses inevitably fail. With Zero Trust, you target optimal security policies to specific business journeys and continuously update them as changing conditions demand. If the old model of security was an inflexible moat and castle, Zero Trust is a modern city where people and commerce flow freely while individual buildings, dwellings, assets, etc. have their own security systems allowing only authorized individuals to enter and access only the floors and resources they need to live, work, and play. Meanwhile, public safety provides watchfulness and response services to identify dangers and address hazards. With targeted protection, the city can locally contain threat impact to a single neighborhood or block, and it is rare for an event to disrupt the entire city. With Zero Trust, organizations can:
- Easily support anywhere-work models. Zero Trust can empower employees with increased choice to work from anywhere with any device as long as they authenticate properly on a compliant device and app. Zero Trust can also empower employees by shifting responsibility for security away from users and instead relying on technical controls to do their work (e.g., using a digital certificate and biometrics to establish identity instead of requiring that employees remember passwords). Instead of forcing employees to use a VPN for connectivity, Zero Trust network access (ZTNA) allows secure connectivity from virtually anywhere without the hassle of a VPN.
- Accelerate cloud modernization. As enterprises seek scale, flexibility, performance, and innovation with cloud services, they are embracing cloud-native technologies, driving agile and DevOps-based tech operations, and upgrading cloud security with Zero Trust. The hyperscalers now embed Zero Trust principles into their environments. In May 2023, AWS debuted its ZTNA service, joining GCP and Azure which both already had it. Google embraced Zero Trust after suffering a nation-state attack a decade ago, and its systems and interfaces today embody Zero Trust principles. Azure uses its position as many organizations’ identity provider to make its systems identity-first and provide one of only a handful of credible Zero Trust “policy engines” as described in NIST SP 800-207. For those still cautious of moving some workloads to the cloud, Zero Trust can alleviate many security and privacy concerns.
- Co-create and innovate more flexibly with partners. Without the benefits of Zero Trust, security teams will resort to providing partners with convoluted access to enterprise data and systems, stifling innovation — if they’re willing to provision access at all. With Zero Trust, because you can limit partner access, protect data with encryption and privacy-preserving technologies, and segment the network, you can enable partnerships while reducing the risk that partners become a source of a data breach or privacy abuse. Examples include data-sharing partnerships for value-added services to consumers or the ability of manufacturers to share data with suppliers to help them streamline and strengthen supply chains.
- Pilot emerging technology with less risk. Healthcare organizations are challenging environments to secure, thanks to the variety of devices attached to their networks, resource constraints, and the fact that mistakes can be life-threatening. Pacemakers, insulin pumps, and other medical devices are becoming more advanced and connected. Meanwhile, new cloud and edge solutions are making it technically easier to move patient care to the home, dramatically increasing a healthcare organization’s attack surface. ZTNA becomes essential for edge deployments and within the hospital itself, as microsegmentation can protect clinical applications from the lateral movement of cybercriminals. In an industry plagued by ransomware and state-sponsored attacks, Zero Trust can ensure that digital transformation continues.
- Protect your AI models. For many enterprises, large language models (LLMs) like ChatGPT, GPT-4, Bing with AI, Bard, etc. will transform their business, generating new revenue, creating new experiences, or helping to cut costs by optimizing existing processes. Cybersecurity teams will need to help data scientists, machine learning operations, and developers to protect fine-tuned models (where your sensitive and confidential data is most at risk) from a number of threats including model theft, inference attacks, data poisoning, and prompt injection. All the core Zero Trust principles of least privilege apply, but enterprises should focus on protecting the data itself with key technologies like homomorphic encryption and differential privacy, and continuous monitoring for suspicious activity.
Zero Trust Improves Customer And Employee Experiences While Supporting Growth
With Zero Trust, security teams can dramatically improve the organization’s security posture, reduce the frequency and impact of breaches, enforce privacy policies, and more easily achieve compliance — just as SaskPower did with its steadfast commitment to incorporating Zero Trust principles. Zero Trust has also become a regulatory mandate and prerequisite to serve certain market segments such as US federal agencies and critical infrastructure firms. However, there are just as many compelling business benefits. With the benefits of Zero Trust security, business leaders can:
- Power frictionless customer experiences. With Zero Trust, security teams design protection from an outside-in perspective, balancing security requirements against hindering UX. Managing identities is a core Zero Trust pillar; it’s also a domain in which security can improve UX, especially by killing off the dreaded password. Passwordless authentication experiences based on biometrics (finger, face, voice, behavior, etc.) support a minimally invasive, low-friction, but secure UX.
- Drive new levels of employee productivity while reducing costs. Zero Trust actively influences all three drivers of Forrester’s Employee Experience Index, which measures engagement at work. Zero Trust fosters empowerment by giving employees the autonomy to work the way they want — from any location and with any device. It also plays an important role in enabling higher productivity through the elimination of cumbersome passwords, replacement of VPNs, and consolidation of performance-draining security agents on devices — all of which also save the enterprise money. Finally, because it enables employees to seamlessly work in ways they never could before, it inspires a good security culture, one where employees don’t actively try to circumvent security policy and they perceive the organization as forward-looking and innovative.
- Better connect and support a globally distributed enterprise. Whether a multinational service provider wants to expand to new offices, a retailer seeks to launch new locations, or a consumer bank plans new branches, each of these sites will need about 18 types of services that provide dependable connectivity, robust bandwidth, and strong security. A Zero Trust edge solution securely connects and transports traffic in and out of sites using mostly cloud-based security and networking services. It’s also a great approach for rapidly integrating the distributed sites and locations of a recently acquired company with a poorer security posture.
- Confidently expand into new markets and serve new clients. Expanding into new geographic markets requires a careful assessment of local risks from IP theft and cyberattacks. With a Zero Trust approach to securing remote offices and employees, enterprises might be willing to take on more risk where others can’t or won’t. Zero Trust makes it easier for businesses to roll out and flexibly support the type of employment model that’s best for the business in a given market or scenario — permanent, part-time/flex, independent contractors, outsourcers, etc. It also allows the business to grow and contract as it needs to as well as suddenly exit markets (e.g., when companies had to suddenly pull out of Russia).
Use Zero Trust To Accelerate Transformation And Promote Its Benefits
To accelerate Zero Trust adoption, it’s up to both business and technology leaders to look for opportunities to integrate it into specific transformation initiatives. Security teams often don’t know how to start their Zero Trust journey. Faced with a mountain of technical debt and a complex environment, they become paralyzed because they erroneously assume they must transform their entire environment. For large enterprises with complex environments, the better approach is to identify specific use cases or initiatives that would benefit from Zero Trust adoption. Zero Trust can help accelerate initiatives like new digital customer experiences, new partnership models, anywhere work, geographic expansion, cloud migrations, and edge computing deployments, to name a few. To help enable Zero Trust programs, executives should:
- Join or help charter a Zero Trust steering committee. This establishes a shared Zero Trust governance structure. The investment prioritization, decision-making, and risk escalation processes formalized within the Zero Trust steering committee shift the success of Zero Trust implementations from the security organization to a more distributed model that aligns with the goals, objectives, and risk tolerance of the broader organization. Business representation and leadership in the Zero Trust steering committee provide insights into the business vision, goals, and challenges that direct the Zero Trust strategy and roadmap and ensure Zero Trust initiatives help power revenue-driving corporate objectives.
- Develop a Zero Trust enablement plan. Given the industry confusion and misinformation, it’s important to level-set key individuals’ understanding and competence with Zero Trust principles and the conceptual architecture. You’ll want a cross-section of business and IT leaders to participate in Zero Trust education workshops. This group of line-of-business leaders, product managers, CX leaders, IT leaders, etc. should gain an understanding of Zero Trust’s benefits and how to apply its principles at a high level. Then conduct more advanced workshops with IT, but don’t limit these to just the security team. Enterprise architecture teams are pivotal to the success of Zero Trust, particularly for developing solution architectures for key use cases. Lastly, you will want cohorts of individuals to pursue Zero Trust certifications.
- Continue to identify use cases and customer journeys for Zero Trust transformation. As you achieve Zero Trust success, build on your initial wins by identifying additional use cases, customer or employee journeys, and other initiatives for new Zero Trust deployments. Many organizations, once they have these initial successes, will then mandate Zero Trust for all new app deployments and software development. Another approach is to identify existing customer or employee journeys hampered by cumbersome security policies and controls; sometimes the most frustrating experiences are the ones that would benefit the most from a Zero Trust approach. What employee support processes are the most inefficient and manual? How burdensome is it for consumers to enroll, authenticate, and engage with your digital experiences?
- Define and track benefits to demonstrate the business ROI of each implementation. For example, one German-based manufacturing organization made Zero Trust part of its workspace transformation program. The program involved replacing all of its assets, enabling bring-your-own-device flexibility for the workforce, and introducing Microsoft 365 across the global business. As part of this refresh, the firm chose Zero Trust as its security model, and the business benefits were clear and well documented with funding streams linked to productivity enhancements and increased agility and choice.
- Chart your course for intermediate maturity. With a series of successes and growing competence with Zero Trust, organizations can develop a more ambitious roadmap to embed it across the enterprise and mature the organization from beginner to intermediate. Both Forrester and the US Cybersecurity and Infrastructure Security Agency (CISA) provide broad outlines for three different levels of Zero Trust maturity; Forrester’s levels are beginner, intermediate, and advanced. Business and technology leaders can use our recommended roadmap to achieve intermediate Zero Trust maturity. It includes nearly 40 tasks and technologies across the seven Zero Trust domains.
- Use Zero Trust for continuous improvement in the future. Soon, enterprises will embed Zero Trust into their architecture, new apps, and even into their development frameworks. Adherents to infrastructure as code are already integrating security policy like microsegmentation into their terraforms and CI/CD pipelines for cloud app deployments. Modern Zero Trust solutions will integrate with multiple concurrent identity providers and incorporate device entity attributes in real time for sophisticated risk scoring. AI will enable enterprises to centralize Zero Trust policy across environments and turbocharge security automation and orchestration. Zero Trust innovation is just beginning. Future fit enterprises realize the Zero Trust journey never ends and will use its principles for continuous improvement in the same spirit as total quality management.
Talk To Us
Discover how Forrester provides guidance and tools to help protect your business and your customers in an increasingly complex risk landscape — without impeding customer experience and growth opportunities.
Thank you!
Ready to learn more now? Give us a call:
Americas: +1 615.395.3401
EMEA: +44 (0) 2073 237741
Asia Pacific: +65 6426 7060