
LAPSUS$ & OKTA: The Cyber Attacks Continue
Lapsus$, a Portuguese hacking group from Brazil, has recently been linked to cyber attacks on some high-profile targets. The cyber gang is best known for publishing sensitive information stolen from major technology companies and governments. The group has boasted breaking into Nvidia, Samsung, Ubisoft and others. How the group managed to breach these targets has never fully been clear to the public. If true, the breach at Okta may explain how Lapsus$ has been able to achieve part of its recent string successes. Thousands of companies use Okta to secure and manage their identities. Through private keys retrieved within Okta, the cyber gang may have access to corporate networks and applications. Hence, a breach at Okta could lead to potentially disastrous consequences.
Lapsus$ commenced its activity in December 2021. Most of its activities are focused around breaching different governmental agencies and technology companies. Since the beginning of its operations, the group has been has been viewed as a “ransomware group”, although its modus operandi so far has been very different from that of a ‘regular ransomware group’, as they do not encrypt the systems of their victims.
Lapsus$ maintains a very active Telegram group, with more than 35,000 subscribers, posting announcements about their breaches completed and stolen data. The real motivation of the group is still unclear however, even if it claims to be purely financially motivated. Lapsus$ has a strong engagement with their followers, and even posts interactive polls on who their next unfortunate target should be.

Figure 1 – Poll results posted by Lapsus$ group on their next targets
The first proclaimed breach by the group was on Brazil´s Ministry of Health and other governmental agencies in December 2021.

Figure 2 – First breach by $Lapsus group of Ministry of Health of Brazil
Since early 2022, Lapsus$ has accelerated its cyber reach and has been involved in the data breaches of several major technology companies across the world, such as NVIDIA, Samsung, Ubisoft and allegedly, Microsoft. The focus of the group on these tech company giants was mostly on source code.

Figure 3 – Source code publications by Lapsus$ group
On March 22, the group announced on its Telegram channel that it had secured access to an Okta admin account, an identity and access management company, including access into various internal systems of the company, claiming that their ultimate goal are indeed the company´s customers, and not the Okta itself.

Figure 4 – Lapsus$ group announcement about OKTA
It is still not clear how Lapsus$ breaches its victims, but based on its publications, there are two possible assumptions:
- Breaches via supply chain – breaching service providers like OKTA in order to get access to its customers.
- Recruiting insiders in big corporations
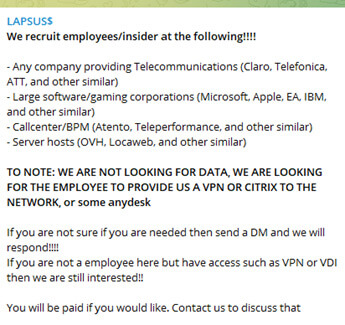
Figure 5 – Lapsus$ group post on March about recruiting insiders
CPR strongly advises Okta´s customers to exercise extreme vigilance and cyber safety practices. The full extent of the cyber gang’s resources should reveal itself in the coming days.










