Abstract
Today information technology has become integral part of every kind of business. Organizations often need experts who have great insights in solving their business problems through information technology. This has led to development of a new field: information technology consulting (or IT consulting). This field has matured quite well in last 20 years. This study is an attempt to identify major focus of IT consulting practices and the challenges associated with them. 123 peer-reviewed academic research papers in field of IT consulting were considered for this systematic literature review. After filtering these papers, eventually 36 papers were selected. A number of major focus of IT consulting in last 20 years and challenges associated with them were identified (Education/IT Training, Auditing, Project Management, Knowledge Transfer, IT Economics, Security, Competitiveness, Applications). This review paper provides valuable information for business executives who are seeking to use IT practices for their business problems. It also provides directions for future research in IT consulting.
You have full access to this open access chapter, Download conference paper PDF
Similar content being viewed by others
Keywords
1 Introduction
Among all developments, the biggest impact on management consulting has been made by Information Systems (IS) in general and Information Technology (IT) in particular (Nolan and Bennigson 2002). It has become a major tool for management consulting companies to deal with central issues of organizations like scenario analysis in strategic planning consulting, managing information of organization in data warehouse, data driven decision making through data mining and business intelligence techniques (Galliers and Leidner 2014). Systems like Customer Relationship Management (CRM) and Enterprise Resource Planning (ERP) introduced by IT consulting firms, have played key roles in management improvements. IS has become de facto necessity for any management firm to achieve sustainable competitive advantage (Clemons 1986).
This study is an attempt to identify key areas for which IT consulting have been used and for achieving a specific outcome. Till now, there is no review article on this interdisciplinary domain, which the current study addresses. The rest of the paper has been structured as follows: Sect. 2 discusses the methodology adopted, Sect. 3 discusses the emerging themes whiles Sect. 4 concludes with directions for future research.
2 Methodology for Systematic Review
This section provides outline for systematic literature review. These outlines include development of review protocol, selection of academic papers and extraction of data.
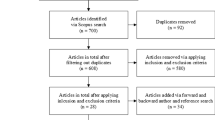
Protocol development is the first step and this step determines the search criteria for academic papers for the purpose of review. Research papers for review were extracted from Scopus database. Specific keywords were used to search these papers. The keywords used for searching Scopus database are Information Technology Consulting, Information Systems Consulting and IT Consulting. In order to extract all possible combinations of search keywords, the Boolean operator “OR” was used. The second step in this process is to take the Inclusion decision on the basis of title of the research paper. This step involved the independent readings of titles of the papers by both authors. Irrelevant papers were filtered out. Many non-English, duplicate, news and commentaries were eliminated in this step. After this step, 75 papers were kept for further filtering process. The third step in this process was creating the inclusion decision on the basis of abstract. This step involved the independent readings of titles of the abstracts by both authors. Despite of the fact that many search keywords appeared in these paper, focus of many papers were found not to be in IS/IT consulting. Such papers were filtered out. After this step, 52 papers were kept for further filtering process. 123 peer-reviewed academic research papers in field of IT consulting were considered for this systematic literature review. After filtering these papers, eventually 52 papers were selected. For the final selection, the two authors read the papers independently. Following criteria were decided for final selection:
Does the study address core aspects of IT/IS consulting?
Are more than one factors from technological factors, management factors, social factors, human factors and organizational factors considered in these studies?
The above criteria lead to shortlisting of 36 papers which could be used for this study. The selection process and the total number of papers identified in each step are illustrated in Fig. 1.
3 Results
Using the 36 research studies selected by the protocol mention in Sect. 2, the title and keywords of the selected research study word cloud was formed as illustrated in Fig. 2 to identify dominant themes in such studies. The key terms in the word clouds are consultants, management, knowledge, information, system and technology. The objective of such an exploration is to visualize how the themes connect with each other among the studies, using tools for text mining.
Subsequently, the association among the words present in the title of selected research studies is identified and illustrated in Fig. 3 using association rule mining. The rules found with the help of Apriori algorithm indicates the nature of association of focus areas within IT consulting literature. The network illustration indicates that focus in such studies is strongly on the consultants along with information technology (or systems) and information management.
The year wise distribution of the selected studies shown in Fig. 4. The highest number of studies had been published in 2016, by looking at the graph it can be said IT consulting is one of the trending topics.
Selected research papers have been reviewed and classified into eight broad categories of trends in IT & IS consulting. This categorization is based on the thematic focus in individual studies. It also provides scope of consulting practices in light of these eight areas. Figure 5 shows distribution of papers across several areas. It is evident from the graphical representation that most popular context touched upon by studies in IT consulting surrounds domains like competitiveness, knowledge transfer and project management. In later subsections, greater exploration would be conducted in each individual area of interest.
3.1 Education/IT Training
New technologies are emerging rapidly in field of IS. People seeking to work in IS to update their knowledge regularly. Most of university students focus on either business or information technology. Those who wish to launch career in MIS or related fields need to have specific skills both in business management and IS. Consulting practicum has potential to help students acquire skills in both areas, thereby enabling smooth transition from university to a professional career in MIS field (Akpan 2016). However it remains interesting to see how this can help people already working in some other fields like sociology, psychology etc. who have good understanding of business environment and wish to move to IS.
Universities offer wide range of courses to business executives to help them understand latest updates in MIS. Often times they focus on more on either business perspective or technical perspective. It lacks proper synergy between research and practice. A framework for integrated approach based on design science research methodology has been developed for teaching professionals IT management and IT consulting (ITMC). This framework has potential to transfer knowledge from researchers working in academia and industries to companies (Boehm et al. 2011).
The Further Education Maturity Model (FEMM) has been developed to aid young IT professionals in selecting right training offerings for them based on their maturity level and quality of training offerings (Boehm et al. 2013).
An Educational Integration Platform Solution (EIPS) which conceptualizes the teaching of IT management and IT consulting as hybrid package of products and services offers a new perspective of ITMC teaching (Boehm et al. 2011). However, impacts of social factors like motivation level of instructors and students remain to be seen.
3.2 Auditing
Information technologies are being deployed in almost every division of organizations i.e. sales, finance, research etc. to aid decision making. So, organizations need to examine and evaluate their IT infrastructure, policies and operations. IT auditing helps organizations in deciding their IT controls. IT auditing requires people who are experts in information security (Felley and Dornberger 2016). It is recommended for students pursuing IS Bachelor or Masters programs to get trained in IT auditing and security aspects of IS as well.
Traditionally role of IT auditors was limited to application control reviews (ACRs) and general control reviews (GCRs). The role has expanded to provide consulting and assurance services on enterprise governance of IT. Therefore, IT auditors should understand business processes and frameworks like COBIT 5 as guideline (Zororo 2014).
Change management and change auditing can be integrated into IT consulting firm’s methodology in order to deal with risks and uncertainties caused by unexpected demands during project period (Chou and Chou 2009).
3.3 Project Management
IT project management deals with planning, organization and delineation of responsibility for successful completion of IT goals of the firm. Traditionally Project Management Information System focused only on scheduling and resource management but now its role is be a comprehensive system that supports the entire project life-cycle, project program and project portfolios. However, such PMIS is expensive, thereby beyond reach of small and medium enterprises (SME). Teixeira et al. 2016 proposes the design process of a PMIS which can improve performance of investment projects and incentives of the firm. This design process can easily be replicated by firms which have similar projects. However, this design process should be tested and validated against other non-investment projects. For successful completion of IT project, establishing effective communication among all stakeholders are of utmost importance. PMIS takes care of this. But now-a-days firms have multiple IT consulting projects at any time. Project teams lacking in multiple task management skills can not deliver desired outcomes on right time. Therefore, adapted techniques of project portfolio management based on portfolio project management, PMIS and project communication management can help in tackling this issue (Kaewta and Chutima 2014).
The hurdle model can been applied to three categories of the IT consulting services such as Idea generation (before the hurdle), Idea execution (after the hurdle) and Project management (both sides) and with effective communication skills IT consultants can better meet their objective (Djavanshir and Agresti 2007). The quality of the consulting services received by the customers can be measure on the basis of the six dimensions such as reliability, responsiveness, assurance, empathy, process and education (Yoon and Suh 2004). Information technology and human resource management oriented tools can be integrated to give rise to knowledge production and it is necessary for the success of knowledge management (Koch 2003). Selection of an appropriate development strategy and the assessment of risk associated with the project are the two major functions for the planning an IS development project (Lesusky et al. 1987).
3.4 Knowledge Transfer
IT project Knowledge transfer deals with transferring knowledge from one part of the firm to the other. It aims to increase productivity by making learning process easier and quicker, thereby reducing the training time. Since learning is social action, social network in addition to incentives have been successfully utilized in knowledge transfer thereby increasing productivity in the ERP sector (Bologa and Lupu 2014). Firms should focus on managing their knowledge network on levels of individual, group, organization and collectives of organizations to facilitate transfer process effectively. IT and organization culture play critical role in this (Liu and Zhao 2009). Knowledge management in consultancies industry had been key to competitive advantage (Kautz and Mahnke 2003). Knowledge management models: reuser, stabilizer, explorer and innovator, can been developed on the basis of the knowledge and service type (Kim and Trimi 2007).
To enable smooth knowledge transfer inside the firm, employees must be willing to share their knowledge with other employees. Therefore, firms should focus on changing perception of their employees about knowledge sharing and provide them motivation and proper communication channel to do so (Hidayanto et al. 2013).
Knowledge management systems help the organization in building the social capital along the three dimensions such as structural, relational and cognitive and enabling the organization for creating and transferring of knowledge (Sherif et al. 2006). The process based on the complex adaptive systems can be used for the creation of knowledge within the organization. This process first identifies attributes for the knowledge assets, than finds relationship among them through association, aggregation, generalization and specialization (Sherif and Xing 2006).
Usually IT users are not familiar with company’s knowledge management framework but till the framework had been used by 2/3 respondents to search for the general information (Kautz and Mahnke 2003). So, the company should focus on its efforts of making its framework familiar to the users.
3.5 IT Economics
Many multinational companies are utilizing IT consulting practices which have been successful in developed economies to developing ones. For successful deployment of such practices in developing economies, complexities of unknown contexts with various risks should be taken into consideration (Wang 2012).
In transitional economies like Serbia, Ukraine, management and IT consulting face problems due to lack of managerial and restructuring experience in a free-market economy. Therefore, important innovation, managerial education and improvement in IT infrastructure are necessary to deal with major problems (Fuxman and Ivanovic 2012).
3.6 Security
Data breaches to firm may lead to business opportunities to IT consulting firms. But it has limitations. It has been highlighted that effects of such security breaches are not limited to the affected firm but also the market value of security consultants are positively associated with the disclosure of security breaches by other firms. Reputation of IT consulting firms can be adversely affected if the number of records breaches is massive (Cavusoglu et al. 2004). This impact becomes even more severe if clients belong to certain industries such as technology and retail sectors.
According to information transfer theory and capital market expectation, clients and investors may hold IT consultation providers responsible for IT security breaches, thereby leading to negative returns (Chen et al. 2012). So, IT firms should have experts for dealing with cyber threat, data breaches or system hacks as advisory to pre-empt such security breaches in organizations. However, this is a less explored domain and is likely to become more critical as an area for exploration in the wake of digitization and the development of cyber-physical systems.
3.7 Competitiveness
IT consulting firms use their resources and capabilities strategically in order to achieve competitive advantage. Among these resources, firm’s knowledge on human resources and their relationship with customers are crucial ones (Calicchio and Marcondes 2016). They also seek to hire top performing consultants. Top performing IT consultants should be able to deliver a good balance of technical skills, functional skills for economic viability and communication skills (Joshi et al. 2010).
Information asymmetry between clients and IT firms lead them to behave in their self-interests. This affects legal and social constraints of engagement between clients and IT firms. Dawson et al. 2010 explains how levels of information symmetry affect the adopted constraint mechanism for engagement between clients and IT firms. Both parties use signal and screen to negotiate. This asymmetry highly affects tacit knowledge-centric projects (Dawson et al. 2016). National culture also play major role in effects of information asymmetry (Dawson et al. 2013).
To move up in career, IT consultants need recognize and build a skill set that can satisfy both personal and other stakeholders’ expectations. It has been noted that top performing IT consultants seems to favor masculinity (Joshi and Kuhn 2007).
The project phases can been divided into seven phases such as pre-project system analysis, project initialization, problem analysis, solution development, solution implementation, project close and post-project system analysis (Becker 2007).
Organizations use information technology to achieve the competitive advantage over the others. So to achieve this, project managers need to plan, select the tools for tracking and monitoring purposes, organize the project for decision making and troubleshoot the project when it is undergoing the difficult phase (Aitcheson 1989).
3.8 Applications
Information is regarded as the major asset by many organizations with can help the organization in long term planning, problem solving, product development and innovation (Harling 1988).
Concurrent-convergent strategy in IT consulting can be used for increasing the client efficiency and for deriving the insights from other information based applications (Liao and Cheung 2003). Both business systems managers along with IS managers should design the new information flows across the enterprises and how it can be used for achieving the business goals (Monheit and Tsafrir 1990). IS facilities the communication of information among the people such as organization are assisting their customers to solve their problems related to services and products offered by the organization (Harling 1988).
Global positioning systems, geographic information systems and remote sensing technologies has been integrated to address the surface environmental issues such as assessment of the groundwater resources (Gibas-Tracy 1996). IS for consulting the passengers with the help of the tools has also been developed (Gance 1996).
4 Conclusion and Future Direction
The main objective of this study was to find IT practices adopted by IT firms for consulting with their clients and issues associated with them. To accomplish this objective, this literature review attempted to identify challenges faced in IT consulting and their solutions to deal with them by various firms and researchers, both in industry and academia. This review found out that majority of research papers follow empirical methodology. Papers which provide conceptual frameworks and theoretical analysis are lacking. Problems like negotiations between IT firms and clients, signaling among firms etc. are challenging to solve using empirical approach. They lack a proper framework which could serve as foundation of any further application. With innovation in IT technologies, malicious practices like fraud, data breach etc. are also increasing, thereby making roles of IT auditors. Currently, there is no proper framework for IT auditors and their roles are vaguely defined. Responsibilities and qualifications of IT auditors need to be clearly identified. Further research needs to be done on cognitive aspects of IT consulting practices because cognitive aspects play key role in acquiring new knowledge and deciding how to design training modules for company employees. Also, many papers provide recommendations for students who wish to work in IT field. More research needs to be done in designing modules/recommendations for people working in non-IT fields and wish to switch to IT fields.
References
Akpan, I.J.: The efficacy of consulting practicum in enhancing students’ readiness for professional career in management information systems: An empirical analysis. Decis. Sci. J. Innov. Educ. 14(4), 412–440 (2016)
Boehm, M., Stolze, C., Breitschwerdt, R., Zarvic, N., Thomas, O.: An integrated approach for teaching professionals IT management and IT consulting. In: AMCIS (2011)
Felley, G., Dornberger, R.: How to Efficiently Conduct an IT Audit–in the Perspective of Research, Consulting and Teaching (2016)
Chou, D.C., Chou, A.Y.: Integrating change management and change auditing into information technology consulting practice. Int. J. Inf. Syst. Change Manage. 4(1), 15–41 (2009)
Zororo, T.: IT governance assurance and consulting: A compelling need for today’s IT auditors. EDPACS 49(6), 1–9 (2014)
Teixeira, L., Xambre, A.R., Figueiredo, J., Alvelos, H.: Analysis and design of a project management information system: Practical case in a consulting company. Procedia Comput. Sci. 100, 171–178 (2016)
Kaewta, S., Chutima, P.: Improvement of project portfolio management in an information technology consulting company. In: IOP Conference Series: Materials Science and Engineering, Vol. 58(1), p. 012012. IOP Publishing (2014)
Bologa, R., Lupu, A.R.: Organizational learning networks that can increase the productivity of IT consulting companies. A case study for ERP consultants. Expert Syst. Appl. 41(1), 126–136 (2014)
Liu, H., Zhao, L.: Knowledge transfer in knowledge network of IT consulting company. In: 2009 International Conference on Information Management, Innovation Management and Industrial Engineering, Vol. 1, pp. 490–495. IEEE (2009)
Hidayanto, A.N., Hapsari, I.C., Alfina, I., Sucahyo, Y.G.: Knowledge sharing perception: Multiple case studies in Indonesian IT consulting companies. JCP 8(10), 2719–2723 (2013)
Wang, Y.: Existing system solutions redeployment in remote developing country: lessons learnt from a multi-national IT consulting firm. In: Cusumano, Michael A., Iyer, B., Venkatraman, N. (eds.) ICSOB 2012. LNBIP, vol. 114, pp. 279–284. Springer, Heidelberg (2012). doi:10.1007/978-3-642-30746-1_25
Fuxman, L., Ivanovic, A.: International applications of knowledge intensive services of management and IT consulting in transitional countries. In: Service Science Research, Strategy and Innovation: Dynamic Knowledge Management Methods, pp. 499–518. IGI Global (2012)
Chen, J.V., Li, H.C., Yen, D.C., Bata, K.V.: Did IT consulting firms gain when their clients were breached? Comput. Hum. Behav. 28(2), 456–464 (2012)
Cavusoglu, H., Mishra, B., Raghunathan, S.: The effect of internet security breach announcements on market value: Capital market reactions for breached firms and internet security developers. Int. J. Electron. Commerce 9(1), 70–104 (2004)
Dawson, G.S., Watson, R.T., Boudreau, M.C.: Information asymmetry in information systems consulting: toward a theory of relationship constraints. J. Manage. Inf. Syst. 27(3), 143–178 (2010)
Calicchio, A.C., Marcondes, R.C.: Relevant factors for competitiveness in information technology consulting businesses. Gestão & Produção 23(3), 625–637 (2016)
Joshi, K.D., Kuhn, K.M., Niederman, F.: Excellence in IT consulting: Integrating multiple stakeholders’ perceptions of top performers. IEEE Trans. Eng. Manage. 57(4), 589–606 (2010)
Boehm, M., Stolze, C., Thomas, O.: Understanding IT-management and IT-consulting teaching as product service system: Application of an engineering model. In: EMISA, pp. 219–224 (2011)
Boehm, M., Jasper, M., Thomas, O.: The Further Education Maturity Model: Development and Implementation of a Maturity Model for the Selection of Further Education Offerings in the Field of IT Management and IT Consulting (2013)
Dawson, G., Li, Y., Zhang, H., Huang, W.W., Watson, R.: Assessing the Relevancy of National Culture in Predicting the Efficacy of Constraints in the Information Systems Consulting Domain (2013)
Liao, Z., Cheung, M.T.: Concurrent-convergent strategy in IT consulting. Commun. ACM 46(9), 103–104 (2003)
Gibas-Tracy, D.R.: Cost-effective environmental consulting using geographic information systems and remote sensing. In: 1996 International Geoscience and Remote Sensing Symposium, IGARSS 1996 Remote Sensing for a Sustainable Future, Vol. 4, pp. 2234–2236. IEEE (1996)
Gance, D.: A new generation of passenger information systems: a single core database and easy tools for consulting (1996)
Monheit, M., Tsafrir, A.: Information systems architecture: a consulting methodology. In: Proceedings of the 1990 IEEE International Conference on Computer Systems and Software Engineering, CompEuro 1990, pp. 568–572. IEEE (1990)
Harling, B.S.C.: Information Systems At Bicardo Consulting Engineers (No. 885155). SAE Technical Paper (1988)
Joshi, K.D., Kuhn, K.M.: What it takes to succeed in information technology consulting: Exploring the gender typing of critical attributes. Inf. Technol. People 20(4), 400–424 (2007)
Becker, J., Niehaves, B., Klose, K.: Political dimensions in IT consulting projects: a governance theory approach. Int. J. Inf. Syst. Change Manage. 2(2), 109–124 (2007)
Aitcheson, G.: Consulting the oracle: A future role for expert systems in IT project management. Int. J. Project Manage. 7(1), 39–41 (1989)
Kim, S.K., Trimi, S.: IT for KM in the management consulting industry. J. Knowl. Manage. 11(3), 145–155 (2007)
Sherif, K., Hoffman, J., Thomas, B.: Can technology build organizational social capital? The case of a global IT consulting firm. Inf. Manage. 43(7), 795–804 (2006)
Sherif, K., Xing, B.: Adaptive processes for knowledge creation in complex systems: The case of a global IT consulting firm. Inf. Manage. 43(4), 530–540 (2006)
Kautz, K., Mahnke, V.: Value creation through IT-supported knowledge management? The utilisation of a knowledge management system in a global consulting company. Informing Sci. 6, 75–88 (2003)
Djavanshir, G.R., Agresti, W.W.: It consulting: Communication skills are key. IT Prof. 9(1) (2007)
Yoon, S., Suh, H.: Ensuring IT consulting SERVQUAL and user satisfaction: a modified measurement tool. Inf. Syst. Front. 6(4), 341–351 (2004)
Galliers, R.D., Leidner, D.E.: Strategic Information Management: Challenges and Strategies in Managing Information Systems. Routledge, New York (2014)
Koch, C.: Knowledge management in consulting engineering–joining IT and human resources to support the production of knowledge. Eng. Constr. Architectural Manage. 10(6), 391–401 (2003)
Lesusky, F.M., Rhudy, R.L., Wiginton, J.C.: The development of a knowledge-based system for information systems project development consulting. Comput. Industr. Eng. 13(1–4), 29–33 (1987)
Nolan, R.L., Bennigson, L.: Information technology consulting. Division of Research, Harvard Business School (2002)
Clemons, E.K.: Information systems for sustainable competitive advantage. Inf. Manage. 11(3), 131–136 (1986)
Dawson, G., Watson, R.T., Boudreau, M.C., Pitt, L.F.: A knowledge-centric examination of signaling and screening activities in the negotiation for information systems consulting services. J. Assoc. Inf. Syst. 17(2), 77 (2016)
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2017 IFIP International Federation for Information Processing
About this paper
Cite this paper
Kumar, A., Grover, P., Kar, A.K., Pani, A.K. (2017). IT Consulting: A Systematic Literature Review. In: Kar, A., et al. Digital Nations – Smart Cities, Innovation, and Sustainability. I3E 2017. Lecture Notes in Computer Science(), vol 10595. Springer, Cham. https://doi.org/10.1007/978-3-319-68557-1_42
Download citation
DOI: https://doi.org/10.1007/978-3-319-68557-1_42
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-319-68556-4
Online ISBN: 978-3-319-68557-1
eBook Packages: Computer ScienceComputer Science (R0)