During the past four months a wave of cyber-attacks has been targeting Israeli companies. The attacks are conducted by different means and target a range of sectors. We estimate with medium to high confidence that Pay2Key is a new operation conducted by Fox Kitten, an Iranian APT group that began a new wave of attacks in November-December 2020 that entailed dozens of Israeli companies.
Read the full report: Pay2Kitten – Fox Kitten 2
The attacker ”Modus Operndi” was to execute a Ransomware attack, potentially to mislead the victim, penetrating to companies’ internal networks, encrypt servers and workstations, steal and leak information, conduct “supply chain attacks” by compromise companies using obtained accessibility or information in breached companies. In October-November we observed a wave of cyber-attacks on industrial companies, and insurance companies. In November we observed attacks on logistics companies.
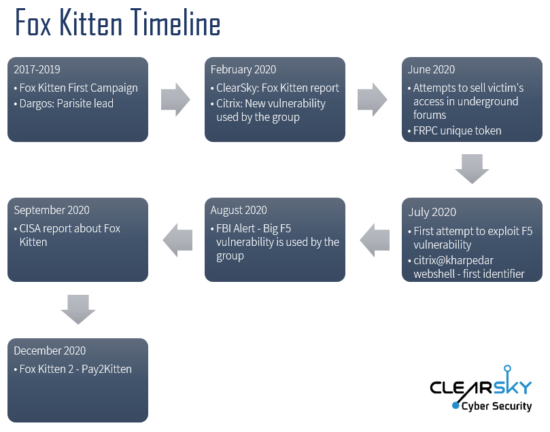
We estimate that this campaign is part of the ongoing cyber confrontation between Israel and Iran, with the most recent wave of attacks causing significant damage to some of the affected companies. The entry vector mostly consists of well-known vulnerabilities covered in our Fox Kitten reports throughout the year. The attacks themselves or the abuse of successful attacks to compromise additional companies or service providers were conducted using obfuscating means, making the discovery of the attack more difficult.
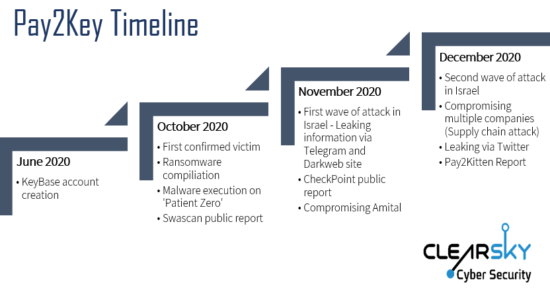
We estimate with a medium level of confidence that this campaign (Pay2Key) is part of Iran information warfare aimed to create panic to Israel and in other countries world-wide. The ransomware group pay2key publicly threatened Israel, this might indicate that this operation is only a propaganda campaign to cause fear with diversion from the real adversary. That would explain the decision to leak the data instead of just demanding ransomware and can explain why this actor chose to leak the data via famous social media platforms and to include threats directed to Israel.
Analyzing the recent attacks conducted by the threat actor Pay2Key led us to the assessment on the overlaps between Fox Kitten to Pay2Key. In the following chapter, we examine the tool set used by Pay2Key group and compare it to Fox Kitten tool set. In the last chapter of the report, we supply a detailed comparison between the two groups based both on technical and thematic analysis.